Template: CIS Controls v8.1
Introduction
This article covers the Center for Internet Security’s Controls v8.1, how they benefit your organization (or a client), where you can access the template in myITprocess, and how to create a review using myITprocess.
What are CIS Controls?
Formulated by the non-profit organization Center for Internet Security, the CIS Critical Security Controls (CIS Controls) represent a systematically prioritized compilation of CIS Safeguards, developed to mitigate the most pervasive cyber threats targeting information systems and networks. These controls are extensively cross-referenced within numerous legal, regulatory, and policy frameworks, underscoring their relevance and applicability across diverse compliance landscapes.
The Center for Internet Security is the organization that frames CIS Controls and CIS Benchmarks, which are globally recognized best practices for securing IT systems and their data.
CISOs, IT security experts, compliance auditors, and more use the CIS Controls to:
-
Leverage the battle-tested expertise of the global IT community to defend against cyber attacks
-
Focus security resources based on proven best practices, not on any one vendor’s solution
-
Organize an effective cybersecurity program according to Implementation Groups:
-
IG1: An organization with limited resources and cybersecurity expertise available to implement Sub-Controls.
-
IG2: An organization with moderate resources and cybersecurity expertise to implement Sub-Controls.
-
IG3: A mature organization with significant resources and cybersecurity experience to allocate to Sub-Controls.
-
What is the difference between the NIST Cybersecurity Framework and CIS Controls 8.1?
The landscape of cybersecurity best practices is vast, encompassing a wide range of scopes, organizational sizes, and industry-specific requirements. Selecting the most appropriate framework for a given organization or client environment can therefore be a complex task. Among the most widely recognized and adopted frameworks is the Cybersecurity Framework (CSF) developed by the National Institute of Standards and Technology (NIST). In addition to the CSF, NIST is also responsible for authoring mandatory standards such as SP 800-53, which outlines recommended security controls for federal information systems and organizations, and SP 800-171, which specifies requirements for safeguarding Controlled Unclassified Information (CUI) in nonfederal systems and organizations—standards that are essential for federal agencies and contractors.
The Cybersecurity Framework (CSF) was developed to serve the vast majority of U.S. businesses—those not subject to mandatory federal cybersecurity regulations—by providing a voluntary, yet strongly recommended, structure for enhancing cybersecurity resilience. The framework is vendor-neutral and introduces a tiered model, comprising four distinct Tiers, to help organizations assess their current cybersecurity posture (Current Profile) and define their desired future state (Target Profile). It is important to note that these Tiers do not represent maturity levels; rather, they reflect the degree of rigor and sophistication appropriate to an organization’s specific industry context and risk tolerance.
For more information, see NIST Cybersecurity Framework (CSF) v2.0.
For many organizations, the breadth and complexity of cybersecurity frameworks can be overwhelming, making it challenging to address every category comprehensively. The CIS Controls framework addresses this challenge by offering a streamlined, prioritized set of actionable recommendations designed to deliver immediate impact. This structured approach enables organizations to initiate the process of securing their environments effectively and to establish a foundational cybersecurity posture.
There are benefits of implementing the CIS Controls for your own or a customer’s environment:
-
Clearly articulated descriptions of each control and sub-control, presented in accessible, non-technical language.
-
Structured to accommodate organizations of diverse sizes, industries, and operational complexities through the use of Implementation Groups (IGs).
-
Designed for ease of adoption and ongoing management, even when initiated from the ground up.
The CIS Controls
The Center for Internet Security (CIS) has established 18 Critical Security Controls, each comprising a set of Sub-Controls, to streamline the development, implementation, and maintenance of a comprehensive cybersecurity program. Each Control addresses a specific domain of cybersecurity and provides targeted guidance for managing associated risks. Similar to the NIST Cybersecurity Framework (CSF), these Controls are broken down into smaller, actionable Sub-Controls, enabling organizations to tailor their cybersecurity efforts to align with their specific objectives and risk profiles.
The 18 CIS Controls
-
Inventory and Control of Enterprise Assets
-
Inventory and Control of Software Assets
-
Data Protection
-
Secure Configuration of Enterprise Assets and Software
-
Account Management
-
Access Control Management
-
Continuous Vulnerability Management
-
Audit Log Management
-
Email and Web Browser Protections
-
Malware Defenses
-
Data Recovery
-
Network Infrastructure Management
-
Security Awareness and Skills Training
-
Security Operations Center (SOC) Capabilities
-
Service Provider Management
-
Application Software Security
-
Incident Response Management
-
Governance (newly introduced in v8.1)
For more information, you can download the entire CIS Security Controls v8.1 standards from here.
CIS Controls in myITprocess
A template within myITemplates gives you the ability to perform an alignment against each Sub-Control. The benefit of myITprocess is that it allows for the creation of reviews based on one, some, or all categories in the template. This gives a Technology Alignment Manager (TAM) the flexibility to perform a review solely based on CIS Controls.
Formatting
Section: The entire template is formatted within one section for ease of use and maintenance.
Category: Each Control is assigned to its own Category in myITprocess due to the hierarchical design of the Standards Library.
Question: Each Sub-Control is assigned its own question in myITprocess. By doing so, a TAM can choose which questions are relevant to the Implementation Group of the review.
Performing a review using CIS Controls is no different than a standard review. Once you apply the section to the customer you wish to review, you can choose the question you need depending on the Implementation Group.
Creating a review
Creating a review and aligning your customers against the best practices of CIS Controls 8.1 is no different than a standard onsite assessment. Rather than reinvent the wheel, the links below will forward you to articles already written on certain topics.
-
Add a new review. During step 6 mentioned in the article on the left, you should select the CIS Controls v8.1 implementation groups. For them to appear there, follow the steps mentioned in the below note.
NOTE You should first add the standard CIS Controls v8.1 IGs. Navigate to Standards page > Add Standard > Add from myITemplates > MSP Cybersecurity Jumpstart, MSP Cybersecurity Fast-track, and MSP Cybersecurity Overdrive and drag these CIS Controls v8.1 implementation groups or implementation groups that are only relevant to you to the standards library on the left. For more information, see Standards Library.
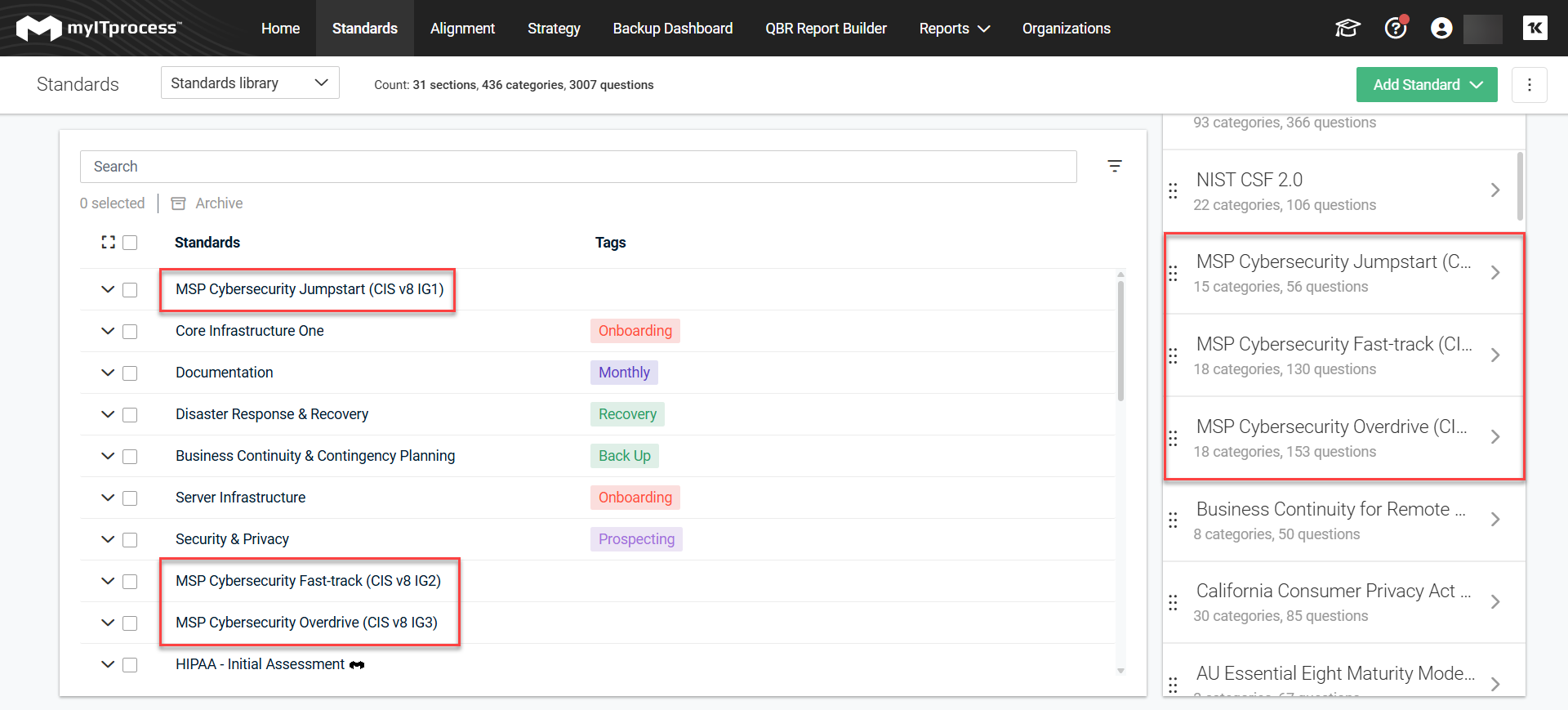
-
Select only the CIS Controls v8.1 section.
-
Determine your target Implementation Group using the CIS Controls (from the PDF doc that you downloaded.)
NOTE myITprocess now has Implementation Group 1, 2 and 3.
-
Once you select an Implementation Group, there are two options:
-
Scroll through the Engineer Technical Analysis and mark non-relevant questions N/A. This will mark them N/A for the vCIO portion and allow them to perform an N/A bulk action.
-
Mark non-relevant questions N/A as the engineer performs the review.
-
-
At the end of the vCIO review, you can opt not to show N/A answers in the Alignment Report. Doing so will prevent non-relevant questions—as well as blank ones—from appearing to the customer.
-
Generate an Alignment Report using only the CIS section and you will have a custom report to show to the client (PDF link at the bottom of this article).